-
Posts
14,876 -
Joined
-
Last visited
-
Days Won
230 -
Speed Test
My Results
mudmanc4 last won the day on April 21
mudmanc4 had the most liked content!
About mudmanc4

- Birthday January 1
Contact Methods
-
AIM
mudmanc4
-
MSN
mudmanc4
-
Website URL
https://lime-it.us
-
ICQ
330539369
-
Yahoo
mudmanc4
-
Skype
mudmanc4
Profile Information
-
Gender
Male
-
Location
In The Plex
mudmanc4's Achievements
-
mudmanc4 started following Ubiquity AP-Pro LED replacement , Total Eclipse of the Sun , Now this one is kinda funny and 1 other
-
 mudmanc4 reacted to a post in a topic:
Richard Lander aka Conuck aka Coknuck
mudmanc4 reacted to a post in a topic:
Richard Lander aka Conuck aka Coknuck
-
 mudmanc4 reacted to a post in a topic:
Trying Out Beta
mudmanc4 reacted to a post in a topic:
Trying Out Beta
-
 mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
-
 mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
-
 mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
-
 mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
mudmanc4 reacted to a post in a topic:
Happy Turkey Day!
-
1 gig fiber Buckeye ?
-
 CA3LE reacted to a post in a topic:
Anyone getting 1000Mbps from Spectrum...not me!
CA3LE reacted to a post in a topic:
Anyone getting 1000Mbps from Spectrum...not me!
-

Anyone getting 1000Mbps from Spectrum...not me!
mudmanc4 replied to MFP21's topic in Show off your speed
I've been loosely following this thread. Not read it all. Keeping this in mind.......... Everything Microsoft has very serious fatal issues. I left Windows after they torched NT/ 2k , everything since stinks on ice with a laser show, on the best brand new shiny hardware with the latest in connection technology. Although I am still forced to deal with it. MS Enterprise is a dumpster fire behind a back water New York City greasy spoon on life support with krok'd out staff. Now that this is out of the way and likely has nothing to do with the topic ......... ----------------------------------------------------------------------------------------- No idea if this has been mentioned in this thread so forgive me, if it were me, first thing I might do is remove all possible hops on internal network. Remove any and all 'other' devices from the local network. Test different times of the day in that setup. I would chill, because I have been around the Sun enough times to know the likelihood of my systems achieving what any ISP sells me are slim. And make the best of what I can do with what I have been granted. Paying for or not. Aside this, if I require a 1 gig service to be 1 gig constantly, then I would get setup with a business account, because I would never fully utilize 1 Gig in my residence unless I was testing for it. Not the way streaming media is setup. Not the way anything residential is setup as far as I am aware. I might go find a local acquaintance and setup an iPerf server between. -
 CA3LE reacted to a post in a topic:
Ubiquity AP-Pro LED replacement
CA3LE reacted to a post in a topic:
Ubiquity AP-Pro LED replacement
-
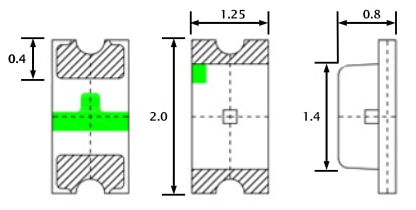
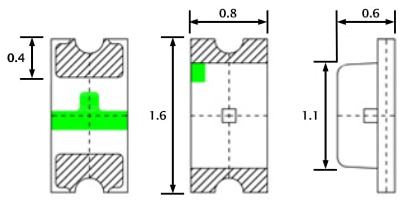
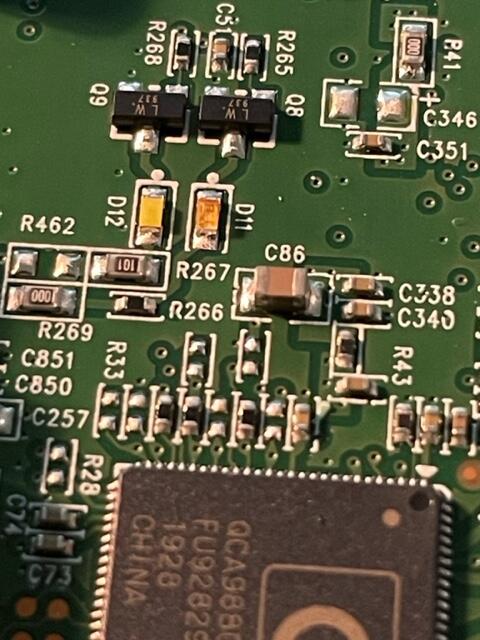
After a couple years the blue LED in the AP-Pro's withered to a mere shadow, not that this really matters for functionality, but it does. It's a status report. Anyway I searched around to find the next size up from the 0603 which appear to be the original size, both the 0805 and the 0603 rates ~3v@ 20Ma. I opted to use the larger of the two. The size of the 0805 claims 2/1.25/.8 mm, where the 0603 sits 1.6/.8/.6 For reference here is the 0805 in my hand , and on a Lowe's gift card. The Anode (+) is the green mark. The job could have used a solder tip 1/4 of the smallest size I had which was ~1.5mm, as well the solder could have been 0.3mm Vs. 0.6mm The blue LED is located at 'D11', the white is 'D12' Below is the before and after replacement of the LED's The new LED floods the lens. At any rate, it was more difficult to spudge the cases open than the LED's were to replace. There is a small amount of silicone type compund around the rim, and three interlocking standoffs on the case. Snapped back together as if they were happy. Before / after This whole thing started after running a CT of Unifi for the controller. They use a version of MariaDB that is no longer maintained, therefore the base OS cannot be updated without hacking together a system. There is a shell script someone came up with that Ubiquity is linking to, I was not entertained. Considering I've used the container to manage the AP's for a while I was ready to update some hardware. The UDM-SE wants to live in front of everything else, considering I'm a PfSense user, that was not going to happen. I gave it it's own physical LAN port on the Netgate 4100 in it's own VLAN, chose to set the DHCP to relay, nothing I've done so far allows the IP's the DHCP server in PfSense lease to the AP clients, to pass data through the UDM. Spanning tree refused to allow me entry to the UDM when setup this way. Turning off RSTP allowed access to UDM (but only from connecting to the UDM.) Loving level2. I'll need to segregate and run a PCAP while a client. So for now the UDM sits on the side in it's own VLAN corner, serving IP's to clients in it's own subnet. The double NAT doesn't seem to effect throughput by any noticeable difference.
-
I wasn't sure how to respond to this saddening news, took me a minute, so here's his laugh and smile for everyone. Whoever remembers what this was about ?
-
 xs1 reacted to a post in a topic:
Wireless router thoughts
xs1 reacted to a post in a topic:
Wireless router thoughts
-
I went ahead with the ASUS RT-AX82U AX5400 Great price on that open box, It's for my Dad, updating from an older netgear, where they don't have all that many devices. If this thing gives him trouble I'll mimic my home network to some extent.
-
 CA3LE reacted to a post in a topic:
Wireless router thoughts
CA3LE reacted to a post in a topic:
Wireless router thoughts
-
Yo, I'm looking for thoughts and infos on wireless routers, maybe mesh, maybe wifi 6 , help me decide.
-
Blue was always download and orange upload, maybe it’s me, been at it for 72 + hours or so.
-
-
 coknuck reacted to a post in a topic:
Tommie Gorman
coknuck reacted to a post in a topic:
Tommie Gorman
-
 tdawnaz reacted to a post in a topic:
Tommie Gorman
tdawnaz reacted to a post in a topic:
Tommie Gorman
-
Ha! I remember when Tommie and I would race to get our post counts up 😆 Wasn't too long before there was no way forward for me to catch up to him. We had our differences , but thats the way it goes sometimes, he’s one that would speak his mind and I liked that about him.
-
 tdawnaz reacted to a post in a topic:
Tommie Gorman
tdawnaz reacted to a post in a topic:
Tommie Gorman
-
 tdawnaz reacted to a post in a topic:
Tommie Gorman
tdawnaz reacted to a post in a topic:
Tommie Gorman
-
Everyone is doing well here still kickin around just no screamin. Sorry for not answering if you messaged on FB, lost access a couple years ago. Seems like every week we lose someone else, guess that happens as we get older. Hope everyone good on your end !
-
How did I possibly miss this! I'll marinate on this for a minute. What happened ? Can we go there ?
-
I left Windows OS after Vista came out, stuck in with XP until it was no longer super viable, I could never 'connect' with the direction they went. Though always have a VM to keep up that I can still use the basics of the OS. Linux / FreeBSD and MacOS have been way more exciting for me since then, where I can tweak it to what I want it to be. Good times either way!
-
Wow, pour one out







.thumb.png.d496c1ee3c2ce31d6207d759b8687b65.png)